Home > Press Release > Establishment of Cryptographic Protocol Evaluation Toward Long-Lived Outstanding Security (CELLOS) Consortium
Establishment of Cryptographic Protocol Evaluation Toward Long-Lived Outstanding Security (CELLOS) Consortium
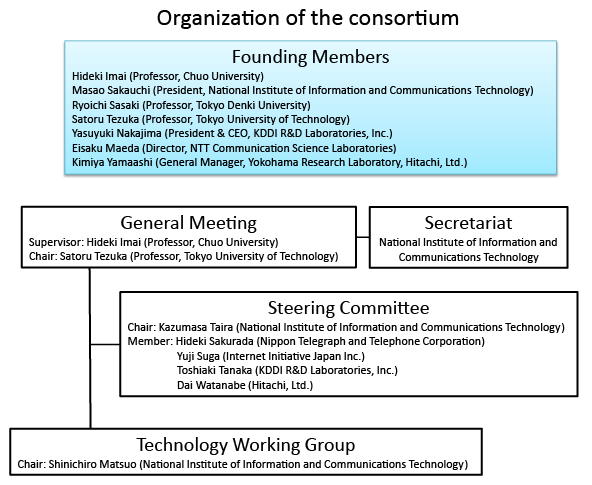
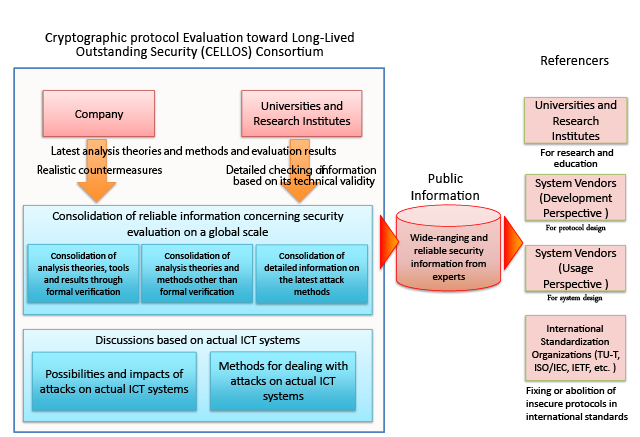
The National Institute of Information and Communications Technology (President: Dr. Masao Sakauchi), Hitachi, Ltd. (President: Hiroaki Nakanishi), KDDI R&D Laboratories, Inc. (President & CEO: Yasuyuki Nakajima) and Nippon Telegraph and Telephone Corporation (President & CEO: Hiroo Unoura), together with experienced experts, companies and organizations both from Japan and overseas, established the Cryptographic protocol Evaluation toward Long-Lived Outstanding Security (CELLOS) Consortium (led by Tokyo University of Technology: Professor Satoru Tezuka). CELLOS strives to improve the security of cryptographic protocols that achieve functions such as authentication and privacy protection with the aim of promoting secure network utilization.
The consortium will consolidate security evaluation information including new attacks against cryptographic protocols and countermeasures against them, and promptly publish the results of examinations conducted by consortium experts. This will help system vendors and network users easily access the cryptographic protocol usage information examined by the experts, which has been difficult for individuals and stand-alone organizations to monitor. Furthermore, since the information can be utilized in determining the feasibility of future cryptographic protocols, it will lead to the promotion and the usage of secure cryptographic protocols and prospects for new ICT systems.
(2) Hitachi, Ltd.
(3) KDDI R&D Laboratories, Inc.
(4) Nippon Telegraph and Telephone Corporation (NTT)
Technical Contact
Shin’ichiro Matsuo
Security Architecture Laboratory
Network Security Research Institute, NICT
Tel: +81-42-327-5782
E-mail: 


Media Contact
Sachiko Hirota
Public Relations Department, NICT
Tel: +81-42-327-6923
E-mail: 


Masayuki Yoshida
Information Planning Department
Yokohama Research Lab., Hitachi, Ltd.
Tel: +81-50-3135-3409
E-mail: 


KDDI R&D Laboratories, Inc.
Tel: +81-49-278-7545
E-mail: 

NTT
Tel: +81-46-240-5157
E-mail: