Summary
Toshiba Corporation, Tohoku University Tohoku Medical Megabank Organization (ToMMo), Tohoku University Hospital, and the National Institute of Information and Communications Technology (NICT) have demonstrated the world's first*1personalized healthcare*2 system that stores genome data from many individuals in multiple locations and utilizes them for medical treatment and healthcare using an information theoretically secure method based on the quantum key distribution (QKD) link, the secret sharing system and personal authentication technology. This system is theoretically secure against the threat of store now and decrypt later attacks, prevents data leaks, falsification, and loss of genome data. In this system, data decryption and reconstruction*3 are performed by using personal authentication and individual consent. The system is expected to contribute to the realization and spread of personalized healthcare.
A part of this work was performed for Council for Science, Technology and Innovation (CSTI), Cross-ministerial Strategic Innovation Promotion Program (SIP), “Photonics and Quantum Technology for Society 5.0” (Funding agency: QST).
Development Background
Treatment of patients has long been provided on the basis of identification of symptoms and disease, plus factors like gender and age. However, advances in genome data analysis technology are opening the way to personalized healthcare that combines an individual’s genetic information with environmental factors, particularly lifestyle patterns, and then calculates risk of disease, and advises on optimal preventive measures. It is an approach with recognizing the diversity of individuals.
However, personalized healthcare relies on analysis of individual genome data and requires strict security in transmission, storage and utilization of personal health data. In Japan, for example, genome data is recognized as a personal identification code that must be treated and protected as such under the Amended Act on the Protection of Personal Information. If leaked, it can pose a multi-generational risk for families, and has to be protected for a span of centuries. Given this, personalized healthcare must be supported by a framework that can accommodate genome data analysis technology, plus secure data transmission and storage of genome data associated with individual IDs, and data decryption, reconstruction and use must be done only with individual consent.
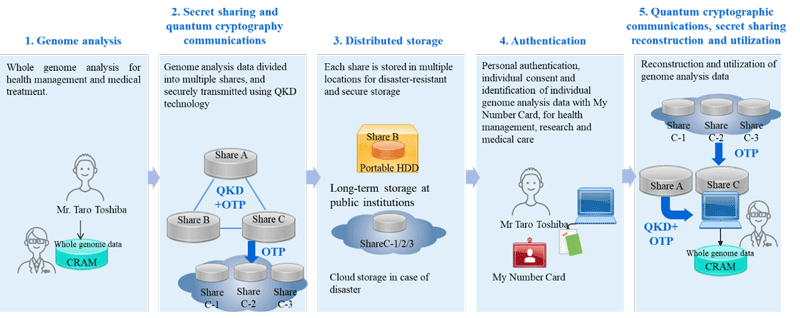
In July 2021, Toshiba, ToMMo, Tohoku University Hospital and NICT used distributed storage technology based on quantum security technology to successfully demonstrate the world’s first experimental backup of large-scale genome analysis data to multiple sites, and their successful reconstruction (announced in August 2021*4). This was achieved by combining the QKD link, which is grounded in quantum mechanics and realizes encrypted communications secure against any attempt at wiretapping or decoding, with secret sharing system, which realizes secure data storage by converting original data into multiple distributed fragments (shares) that look like random numbers. However, this backup method focused on bulk transmission and the storage of large-volume data. Managing individual genome data for many people is much more difficult. In addition, the functions of the QKD and secret sharing systems were implemented and carried out independently of one another, as it is difficult to operate them as a unified large-scale system. The next step was clear: to develop a technology for efficient operation of large-scale systems.
Features of This Technology
The four partners have now done this by developing an integrated key management and share control system. They have demonstrated its ability to advance personalized healthcare with a use case that demonstrates secure storage and reconstruction of bulk genomic data, plus storage of genome data on numerous individuals in multiple locations, that can be reconstructed as and when necessary, with personal authentication.
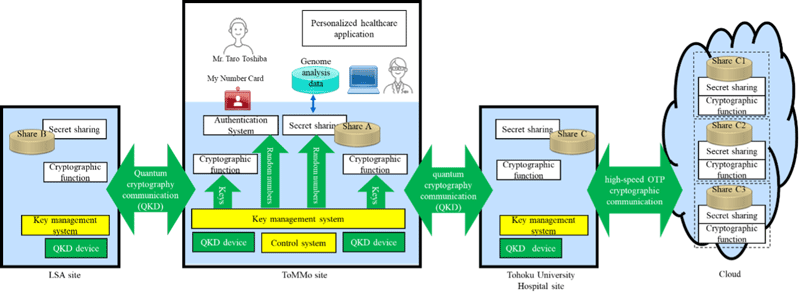
The integrated platform provides unified management and operation of quantum cryptography, secret sharing, and personal authentication. It integrates functions for generating cryptographic keys and random numbers, which are used in large numbers in quantum cryptography and secret sharing, and achieves unified operation of data transmission and storage. As it provides cryptographic keys and random numbers in the same format, and they can be used interchangeably, it realizes highly efficient operation of a large-scale system.
Transmission of large volumes of genomic data requires a large number of quantum encryption keys, but the speed at which they can be generated is limited. Until now, distributed backup systems that store multiple shares at multiple locations have done so at fixed locations. However, the current use case requires distributed storage of large volumes of data on individuals at any given time, which would prevent efficient use of quantum cryptographic keys. The new share control system uses information on remaining quantum encryption keys at each distributed location to determine optimal storage locations, and associates the information with individual IDs. This realizes efficient, secure storage of large volumes of personal data at multiple locations in a large-scale system, and also facilitates data reconstruction and secure use by using personal authentication to identify and reconstruct specific shares.
By linking the distributed data storage technology demonstrated in July 2021 and integrating it with the newly developed key management system and share control system, the four parties have established a personalized healthcare system. Authentication of individuals and personal genome data sharing and reconstruction is based on the My Number Card, an individual ID card issued by the Japanese Government. Genome analysis data cannot be reconstructed at medical centers without the cardholder's consent, preventing information leakage. Demonstrations at ToMMo and Tohoku University Hospital have confirmed the feasibility of this information-safe, practical personalized healthcare system, that can also reconstruct data from shares stored at other sites if data is lost at one site due to a disaster.
Project Structure
Toshiba: Development, construction and operation of QKD system and personalized healthcare system
ToMMo and Tohoku University Hospital: Provision of a verification base, application in individualized healthcare use cases, operation and confirmation of effectiveness
NICT: Development and operation of high-speed one-time pad*5 (OTP) technology and high-speed secret sharing technology
Future Prospects
Toshiba will continue to advance R&D of QKD technologies, including system demonstrations combined with secret sharing technology, and promote early practical application of QKD technologies in various applications, such as medicine, finance, public administration, and communications infrastructure.
ToMMo and Tohoku University Hospital will continue to promote the use of safe and secure ICT technology to realize future-oriented medicine based on genome information and personalized healthcare.
NICT will continue to engage in research and development of quantum communications technologies such as quantum cryptography and optical quantum control in order to contribute to advanced and fundamental research and development and quantum industry.